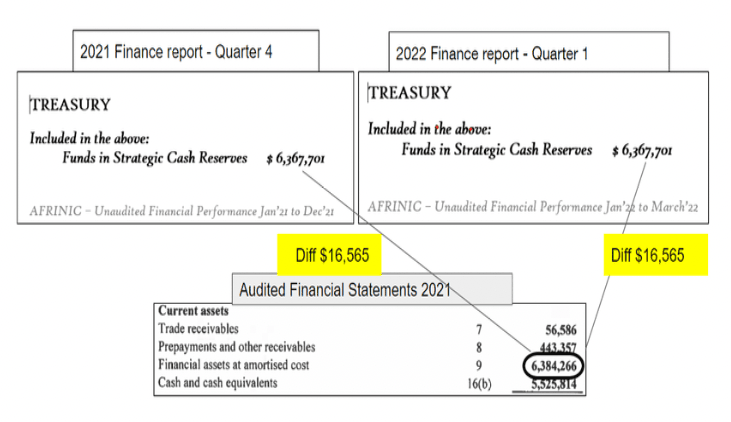
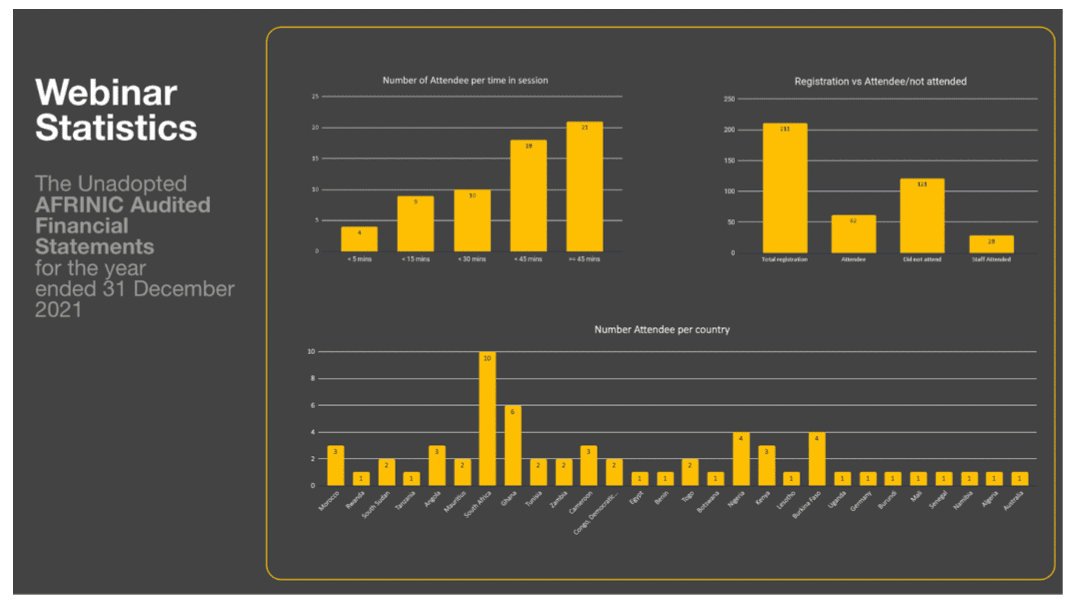
The recently concluded Annual General Member’s meeting raised queries over the AFRINIC Audited accounts for 2021. We wrote to our Resource Members and collected several questions on the Finance audit. Out of which, a few questions came through, and valid responses were given. The Team felt that it would be essential to hold a webinar to better engage with our Resource Members on matters of finances.
The webinar will take place on 21st July 2022 at 12:00 UTC on the Zoom Platform and will provide an update based on the following agenda:
- Audit report for the financial year ended 31st December 2021.
- Questions on mailing lists concerning the financials.
- Way forward
This is a closed meeting, and all Resource Members are invited to engage in the webinar.
Registration for this webinar will be available on the MyAFRINIC portal and the Members’ Discuss Mailing List.
Why it matters
With the finances for 2021 not adopted, this will mean that we will seek to have our membership adopt our finances at the SGMM. Section 115 (5) of the Companies Act 2001 provides that where the financial statements are not approved at the annual meeting, they shall be presented at a further special meeting called by the Board.
Usually, a financial statement would not be approved at an annual meeting if, by the time the meeting is being held, the company had not yet received its audited financial statement. Under these circumstances, section 115(5) of the Companies Act 2001 caters for a company to present its audited financial statement once it is available. In our case, it is different. The member base has simply rejected the audit exercise conducted by the company’s auditor, which has thus given rise to an unprecedented situation, not to mention the reputational risk associated with it.
Be that as it may, AFRINIC does intend to file audited finances for the financial year ended 31 December 2021 in line with best corporate governance practices. For that, AFRINIC requires the collaboration and understanding of its key stakeholders.
This is also following the AFRINIC Bylaws:
7.6) The Registered Members and Resource Members shall, at Annual General Members’ Meetings or by way of written resolutions, in addition to the rights conferred by Articles 7.1 and 7.2, have the right to:
- consider and adopt by Ordinary Resolution the financial statements of the Company;
- receive any auditor’s report;
- consider the annual report;
- determine, by Ordinary Resolution, the general policies for fulfilling the objects of the Company;
- approve, in accordance with Section 130 of the Act, a major transaction;
As such, it is essential to have as many resource members, if not all, in the webinar. This will help us respond to your queries and clarify issues related to the AFRINIC Audited 2021 finances and await the adoption of the audit in the Special General Members Meeting (SGMM), whose date is yet to be announced.
An approximate timeline of activities
Based on the prevailing situation in AFRINIC, this is the probable plan of activities leading to the SGMM. The timeline of activities below is presented as:
| Probable Date/Month | Activity |
|---|
| 21st July 2022 |
AFRINIC Finance Webinar |
| Subject to AFRINIC having a properly constituted board of directors |
Special General Members Meeting for the adoption of the 2021 finances. |
We hope to see you in the upcoming webinar and other subsequent events, as your participation is essential for the digital growth of Africa.
Should you have any questions, please contact: This email address is being protected from spambots. You need JavaScript enabled to view it.